
Enterprises must get serious about data governance - Ecosystm
Do you know what data your organisation is collecting, who is collecting it, what it's used for, where it's stored and whether it's adequately protected against incursions and infiltrations by hackers and cyber-criminals?
If you answered yes to all of the above, then congratulations.
It's likely your enterprise has a rigorous data governance policy in place and – more importantly – has put it into practice.
The majority of Australian enterprises we speak to aren't at this point yet and it's to their detriment.
We do see large financial institutions making a good fist of it, given the size and scale of the data, both structured and unstructured that they have to deal with.
Working in their favour is the fact that they have access to the IT and management resources to do so.
And with regulatory bodies including APRA monitoring their operations, they have a strong incentive not to get things wrong.
Let us look at data classification, as an instance.
The global Ecosystm Cybersecurity Study looks at what organisations classify as sensitive data and most organisations in Australia fail to identify sensitive data beyond IP and legal requirements.
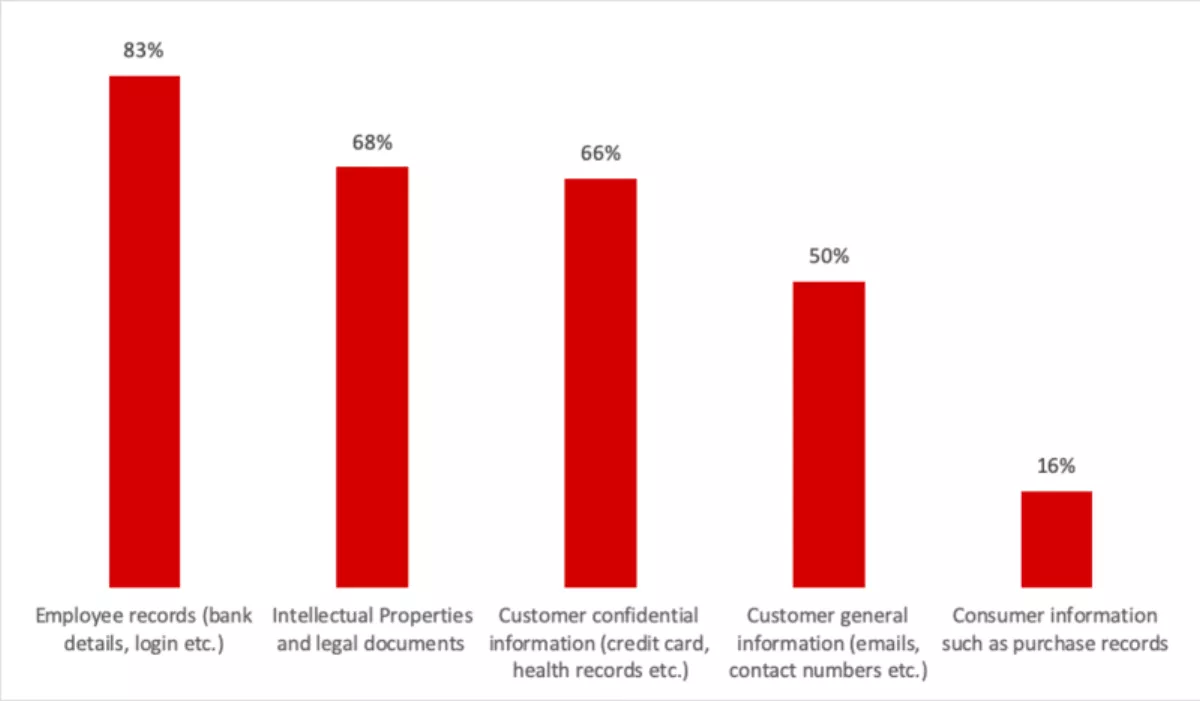
Source: Ecosystm, August 2019. N=109
There are other areas of concern as well – nearly 47% of organisations believe that public cloud has adequate security with no need to supplement it, and only about 10% of organisation encrypt their sensitive data on cloud.
Other organisations' attitudes and arrangements range from average to apathetic.
Some put appropriate measures in place in their head offices but let things slide in their subsidiaries or branch offices.
The enterprise which has it nailed from end-to-end is a rarity.
Rising risks
Does it matter?
The answer is yes, very much. Just as health records being found in a dumpster was a risk in the 20th century, the risks of sloppy data management are real and rising.
They include the likelihood your enterprise will have sub-optimal processes in place, courtesy of the fact you don't understand your data and are failing to exploit it in full to drive business outcomes.
In the digital era, that's something few businesses can afford to do.
You're also taking your chances with the government regulators charged with ensuring consumers' privacy isn't compromised by businesses' sloppy handling of their personal information.
Latterly, the size of the penalties these bodies are able to impose has increased exponentially.
In Australia, the Office of the Australian Information Commissioner, the national privacy watchdog, is able to impose fines of up to $1.8 million on organisations which are responsible for serious or repeat data breaches.
Australian businesses whose customers are citizens of the European Union may also be subject to that body's much more stringent and punitive GDPR privacy regime.
It allows for maximum penalties of up to 20 million Euros or four per cent of annual global turnover to be imposed on large organisations which breach the privacy of its citizens.
Thirdly, if your data governance is poor, your enterprise is even more of a prime target for hackers and cyber-criminals who are nothing if not opportunistic and understand, all too well, the value of sensitive corporate and customer information.
Failing to manage and store your data securely is akin to putting out the Welcome mat – and the price of 'entertaining' your unexpected guests may be higher than you're willing or able to pay.
Do you want to be the one to tell the CEO he is about to be on the news, and potentially fired for a data breach?
Getting to grips with the issues
Not sure where and how to begin improving the way you do things? Here are some tips for organisations looking to put effective data governance policies and practices in place.
- Know and understand all of the information in your business ecosystem. A comprehensive data audit is a good place to start. It should document the data you collect and keep, internally and externally, who has access to it, how it can be used and where it's stored.
- Educate your stakeholders as to why it's important and make them part of the solution. The popular perception that data governance is an IT issue has become outdated. Marketing, human resources and production should all be involved in managing the data that increasingly drives their operations.
- Prevent your strategy from becoming outdated by making it a flexible one which can incorporate new sources, uses, and security of data as they emerge.
Time to act
In 2019, practically every enterprise in Australia is a data-driven one, from SMEs which maintain a basic customer database up to the Big Four banks which collectively husband hundreds of billions in wealth and data points.
Implementing rigorous data governance policies and procedures may be a complicated and expensive process but the cost of not acting can be even greater.
It's time Australian executives asked themselves whether it's a price their organisations can afford to pay.

