
Radware reports web DDoS attack activity
The frequency and intensity of the new generation of HTTPS floods have increased dramatically, and the sophistication introduced by attackers is growing quickly. In the first half of 2024, web distributed denial of service (DDoS) attacks saw a significant increase in frequency and intensity. A good portion of this activity can be attributed to hacktivists motivated by political tensions. Today's hacktivists are known to reach for more sophisticated L7 attacks targeting online applications, and new vectors such as HTTP/2 Rapid Reset and Continuation floods are taking these attacks to new heights in intensity and duration.
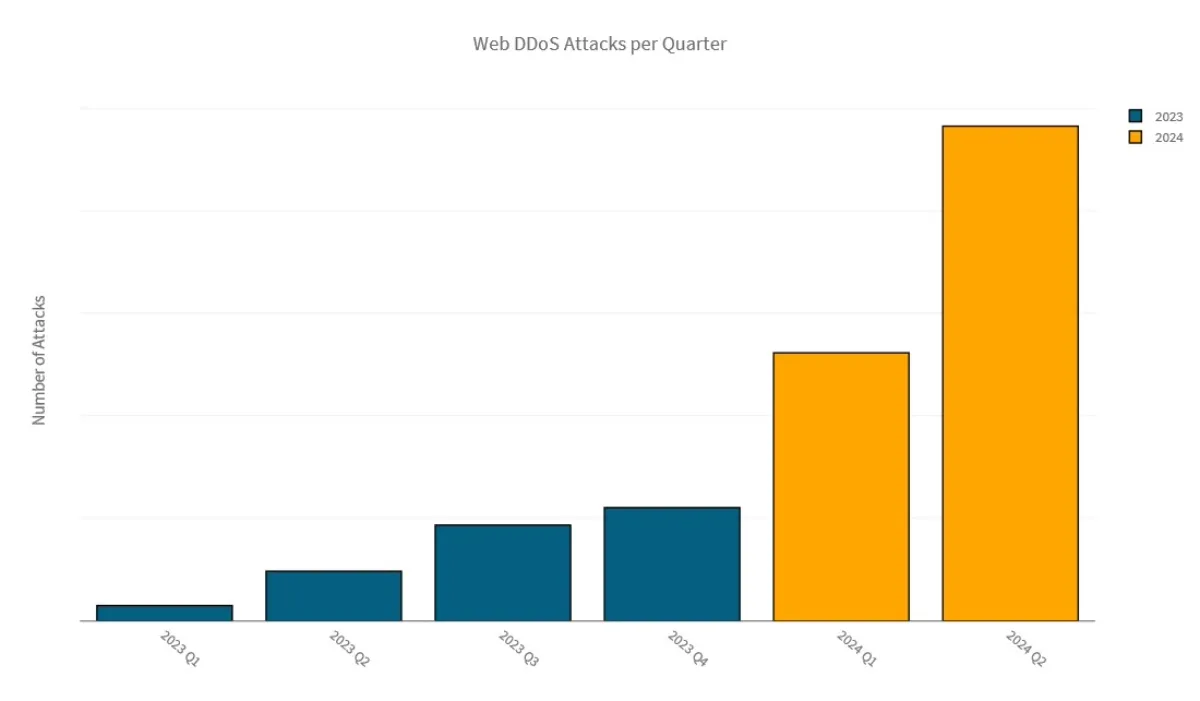
The number of Web DDoS attacks blocked by Radware's Cloud Protection Services increased almost exponentially in 2024. In Q1 2024, the number of mitigated Web DDoS attacks increased by 137% compared to Q4 2023. In Q2 2024, the number of Web DDoS attacks increased again with 85% compared to Q1 2024.
The majority of Web DDoS attacks targeted organizations in the EMEA region, influenced by geopolitical conflicts and significant events like the EU parliament elections, Euro 2024 in Germany and the 2024 Olympic Games in Paris.
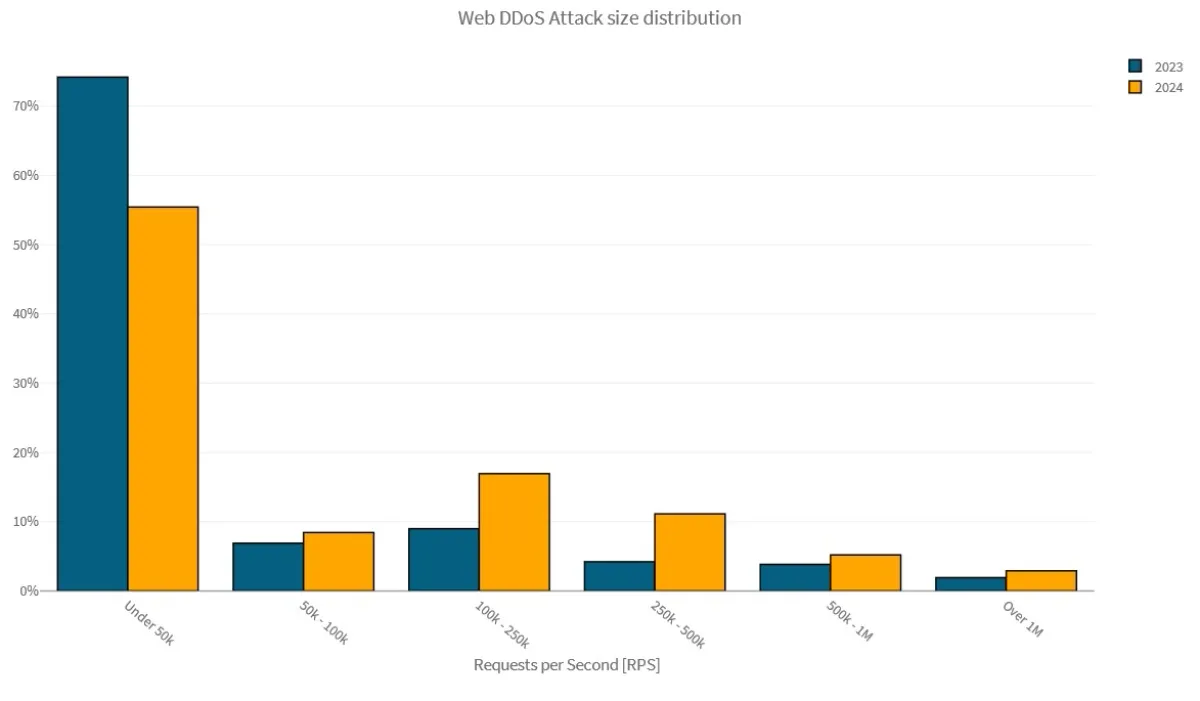
Attack traffic patterns targeting organizations in our cloud demonstrated a shift to larger, more intense and more impactful Web DDoS attacks in 2024.
Application-layer DNS DDoS Attack Activity
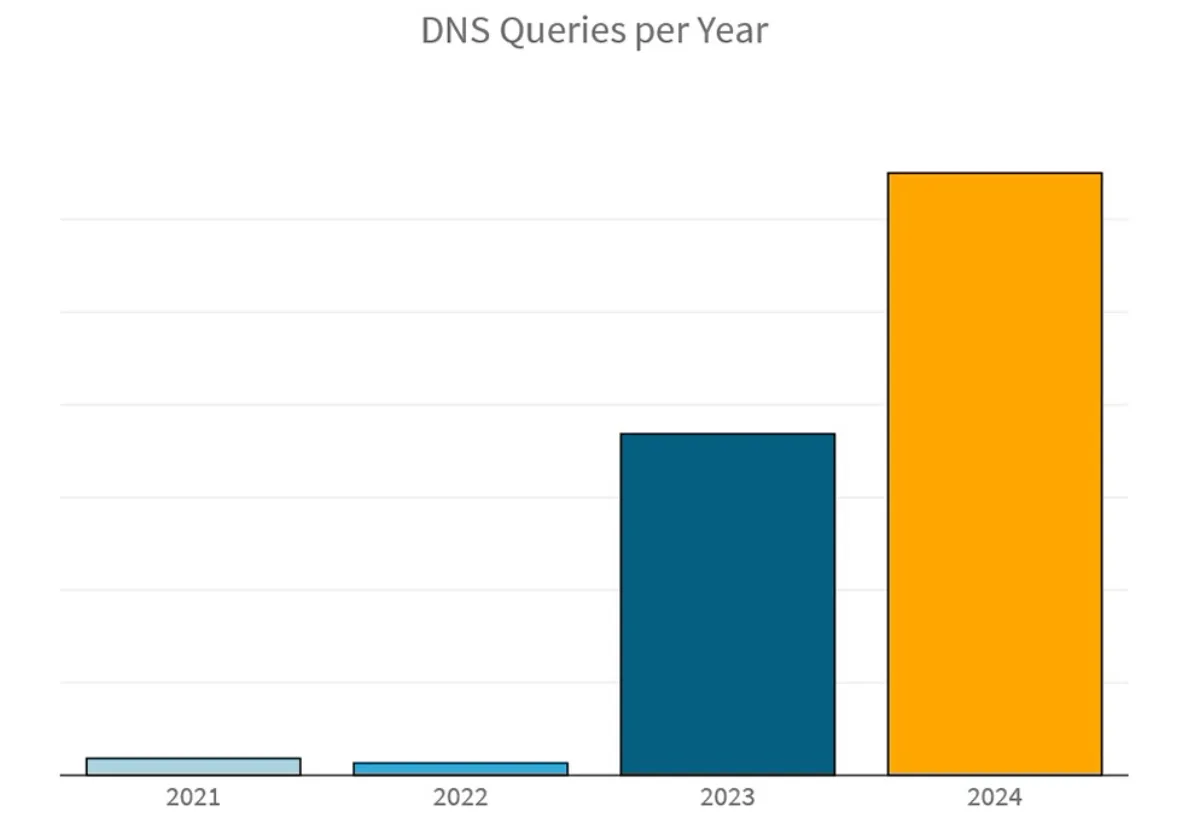
The number of malicious DNS flood queries in the first six months of 2024 has already increased by 76% compared to the total number of queries observed during the whole year in 2023.
Application-layer DNS DDoS attack activity tripled between 2022 and 2023 and quadrupled between H1 2023 and H1 2024. Finance was the most targeted industry, representing 52% of the total DNS query flood attack activity. Technology, telecom, healthcare, and research and education were other notable industries. Most large application-layer DNS flood attacks in the first half of 2024 leveraged DNS-A requests.
Network-Layer DDoS Attack Activity
Network-layer DDoS attacks, which actually span L3 and L4, also exhibited a rising trend in H1 2024.
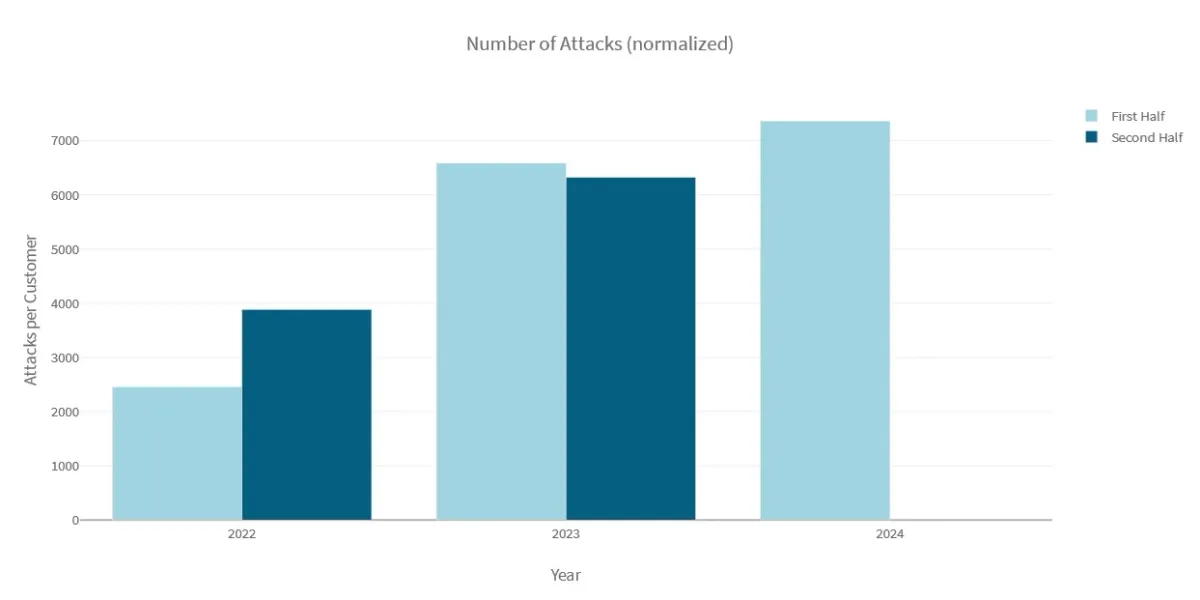
The average network-layer DDoS volume blocked per organisation in H1 2024 grew by 81% compared to H2 2023 and by 205% compared to H1 2023. The network-layer volume blocked per organisation in H1 2024 was 14% higher compared to the network-layer volume all of 2023.
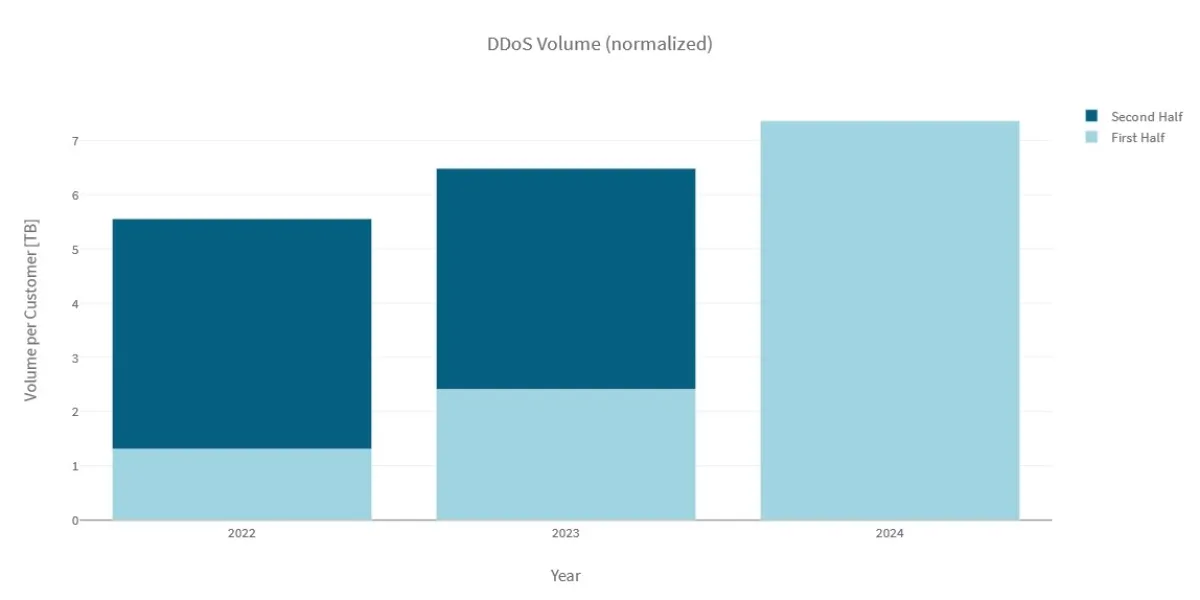
In H1 2024, Radware's Cloud DDoS Protection Services mitigated an average network-layer attack volume of 1.23TB per month per organisation. This represents an increase of 127% in the average network-layer DDoS volume blocked per organisation per month between 2023 and 2024. In contrast, the increase in average network-layer volume blocked per organisation per month between 2022 and 2023 was 17%.
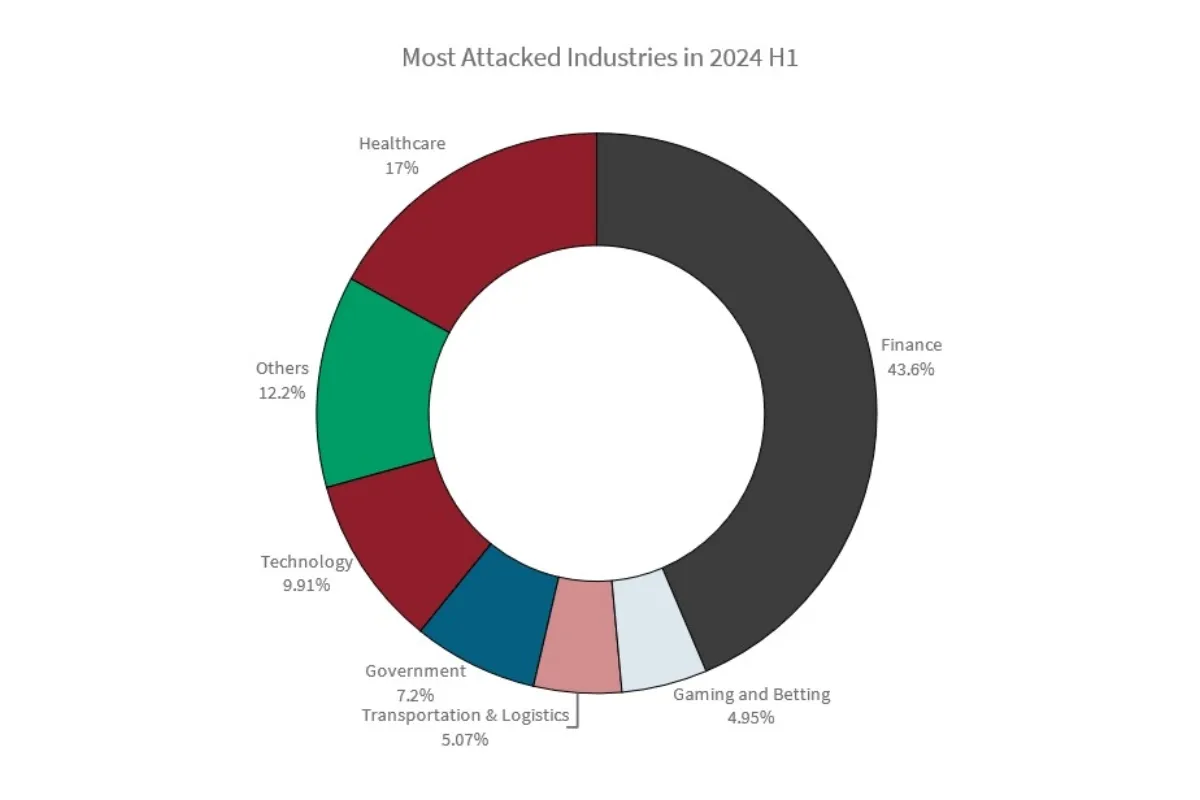
Finance organisations experienced the highest network-layer attack activity, followed by healthcare, technology, government, transportation and logistics, and gaming.
DNS and NTP were responsible for 87% of the total network-layer amplification attack volume. DNS, HTTPS and SIP were the most targeted applications by network-layer DDoS attacks.
Hacktivist DDoS Attack Activity
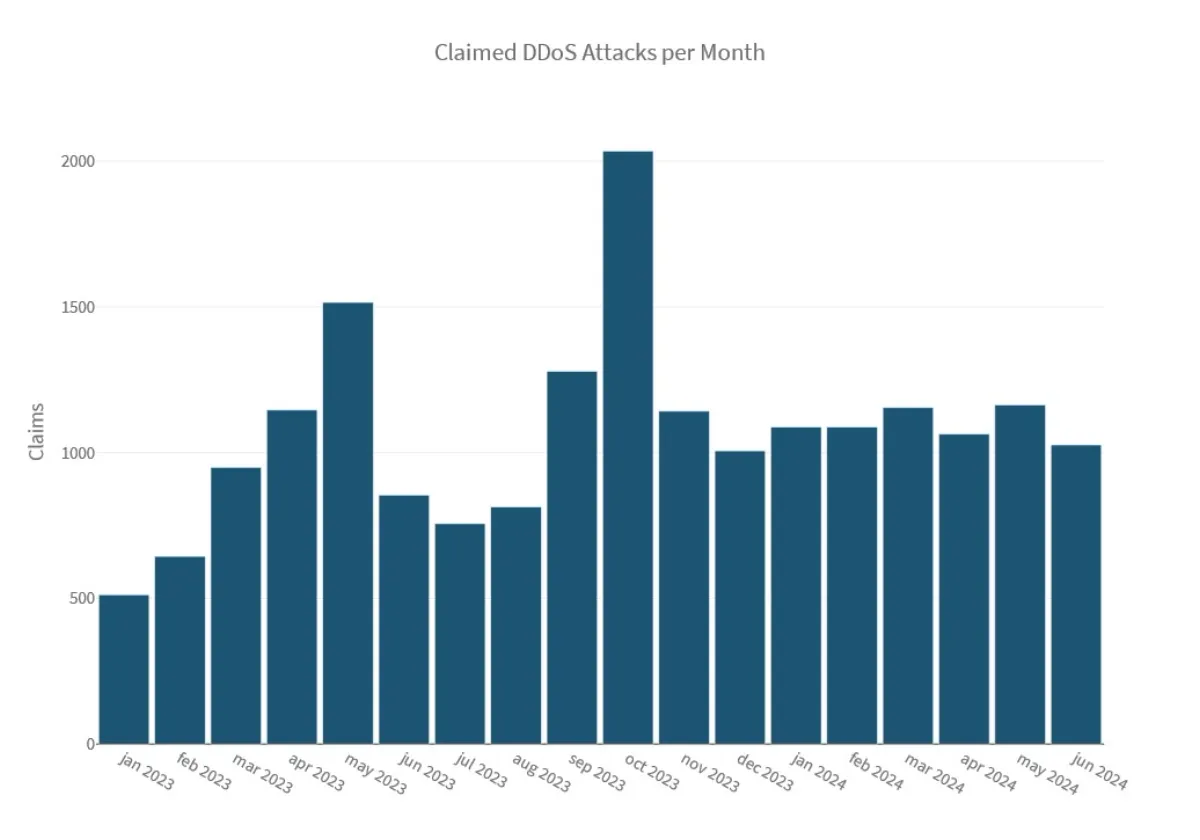
The hacktivist landscape remained dynamic with constant DDoS activity. Hacktivist-driven DDoS attacks hovered between 1,000 to 1,200 claimed attacks per month in 2024 with Ukraine being the most targeted country.
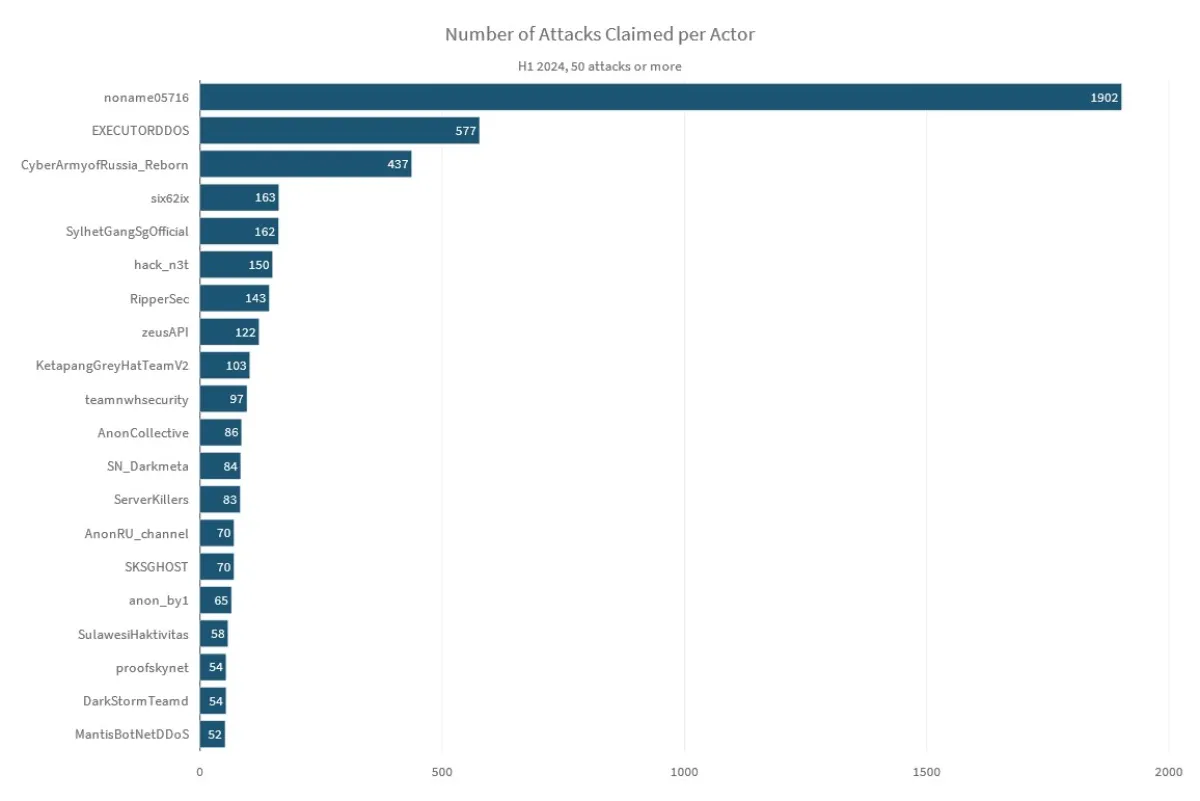
Pro-Russia hacktivist group NoName057(16) remained the most active threat actor. With a total of 5,287 DDoS attack claims since January 2023—of which 1,902 claims took place in the first half of 2024—NoName057(16) leaves the other actors behind by a significant margin. The Cyber Army of Russia Reborn, Anonymous Sudan, Mysterious Team, Executor DDoS and Team Insane PK have been the most active threat actors since January 2023. 62IX, Sylhet Gang, HackNet and RipperSec were among the most notable hacktivist groups in the first half of 2024 alone.
During the first half of 2024, the pro-Russia hacktivist actor group NoName057(16) was observed joining and creating multiple alliances— some temporary, others more permanent. One of their collaborations, with the Cyber Army of Russia Reborn, resulted in a significant amount of attack activity targeting Ukraine, doubling the activity in Ukraine compared to what was observed in 2023. Although Ukraine was only the fourth most targeted country in 2023, it became the most targeted country during the first half of 2024.
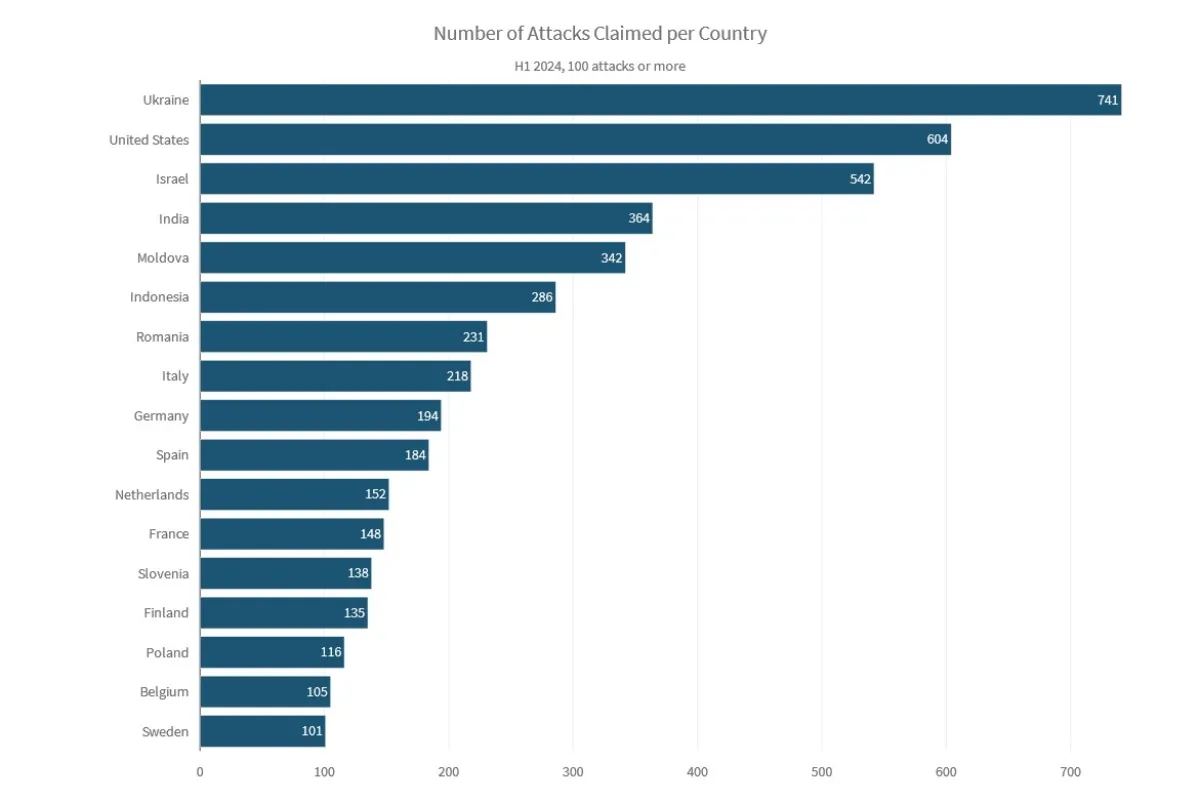
In South Asia, India observed many claimed attacks from Indonesian and Bangladeshi hacktivists, with Anonymous Susukan, Ketapang Grey Hat Team and Sylhet Gang claiming the most attacks. Pakistan was also one of the most frequently attacked countries, mostly by Indian hacktivists Team NWH, Dark Cyber Warrior, Kingsman, Hacktivist Vanguard and Team Network Nine.
The United States became an important target for DDoS-as-a-service providers that like to leverage big, highly visible organisations as a target for their proof-of-capability advertisements. The Telegram groups Channel DDoS v2, ZeusAPI Services and Krypton Networks claimed the most attacks targeting the United States.
The top attacker collectives targeting Israel included RipperSec, 1915 Team, Sylhet Gang, Anonymous Muslims, LulzSec Indonesia, Team ARXU, StarsX Team and Dark Storm Team.
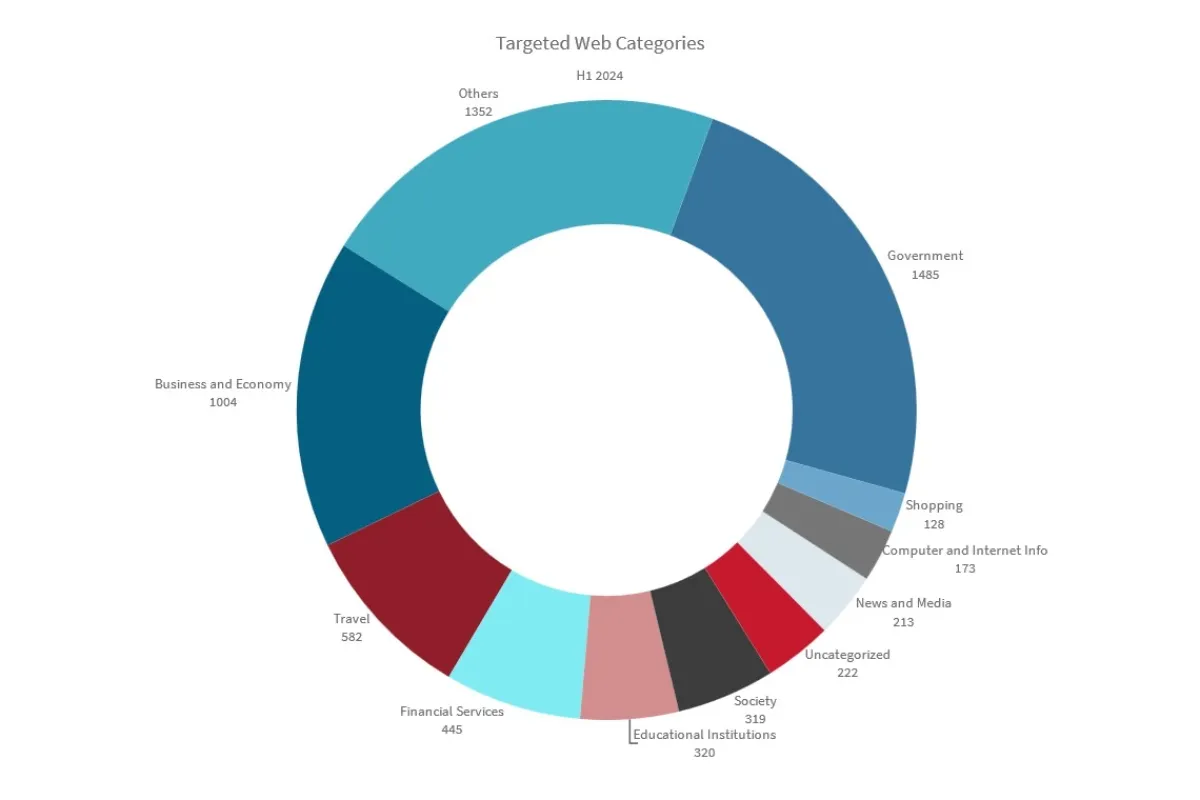
Government websites were the most targeted web category since January 2023.
Reasons for Concern
The first half of 2024 both continued and accelerated on trends we observed in 2023. As geopolitical tensions grew around the globe, AI technology democratised through the adoption of increasingly powerful and publicly available LLM models by threat actors. With indications of a decelerating financial market and an upcoming pivotal election in the history of the United States, we anticipate continued high levels of global activity and a perpetually evolving threat landscape.

