
How to neutralise a web DDoS tsunami attack
Organisations today are facing an urgent imperative to evolve their defensive strategies to keep pace with an aggressive new type of DDoS attack—also known as the Web DDoS Tsunami. Contemporary protection against this new form of HTTP Flood attack requires more than just responding to the attacks; it demands pre-emptively neutralising them to ensure a safe space for business operations and legitimate users.
Unlike their earlier predecessors, Web DDoS Tsunamis aren't settling for intense (but transient) bursts of simple pings or flooding ports at layer 3 or layer 4. Instead, they're bombarding layer 7 (L7) and scaling up in volume and intensity. The real-world attacks involve multiple waves, escalate quickly - sometimes reaching several million requests per second (RPS) - last for hours, and span days. To make matters even more challenging for security teams, Tsunamis cleverly avoid detection by mimicking legitimate traffic and employing tactics like randomising headers and IP spoofing.
A Real-World Story
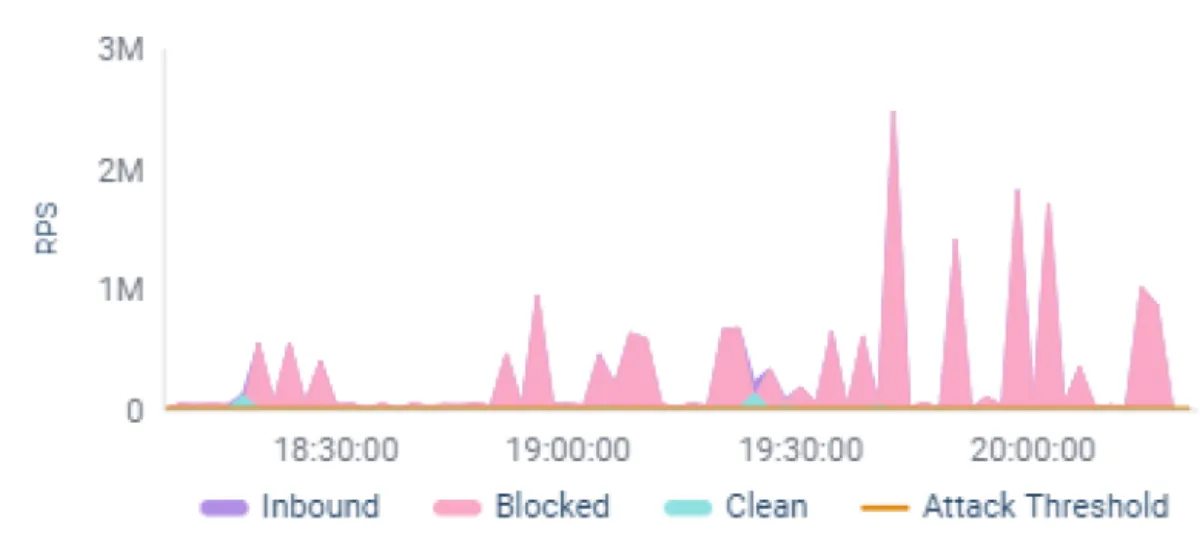
Recently, my company observed firsthand the volumetric and persistent nature of Web DDoS Attacks during an incident at a major insurance company. The company experienced several large-scale attack waves, reaching hundreds of thousands of RPS, with multiple waves peaking at more than 1 million RPS. The largest assault reached 2.5 million RPS. The attacks far surpassed the company's typical traffic rate of several hundred RPS, overwhelming its application infrastructure and disrupting operations.
To make the situation even more complicated, some of the attack waves witnessed have combined network-layer volumetric attacks, exceeding 100 Gbps in data volume. The attack vectors included Web DDoS Tsunami attacks, DNS floods, DNS amplification attacks, UDP floods, UDP fragmentation attacks, NTP floods, ICMP floods, and more.
One of the attacks, represented in the chart below, consisted of multiple waves during a three-hour period with several peaks reaching 1 million RPS and multiple spikes topping 2.5 million RPS.
How to Defend Against a Web DDoS Tsunami Attack
Organisations using traditional defence tools are falling victim to these attacks, leaving them wondering why their existing solutions are faltering.
Traditional network-based DDoS protection and web application firewalls (WAF) weren't built to protect against the new Web DDoS Tsunamis without disrupting legitimate traffic. A proper defence requires a L7, behavioural-based solution that can adapt in real time, scale to a magnitude higher than an on-premises solution and identify attacking requests without blocking legitimate traffic. That type of detection requires decryption and deep inspection into L7 traffic headers, which network-based DDoS protection solutions are unable to provide. At the same time, WAFs that rely on signature-based protections are ill-equipped to deal with the randomised, dynamic sophistication of the Tsunami.
So, what's the right response to high RPS Tsunami attacks? Instead of a volumetric approach that doesn't distinguish between good and bad traffic, the proper solution must accurately distinguish between legitimate and malicious attack traffic surges. More specifically, the solution should automatically:
- Minimise false positives – Dedicated AI-driven, behavioural-based algorithms are needed to quickly and accurately detect and block L7 DDoS attacks without interrupting legitimate traffic.
- Prevent advanced threats and zero-day attacks – The solution should protect against a wide range of L7 DDoS threats, including smaller-scale, sophisticated attacks; new L7 attack tools and vectors; and large-scale, sophisticated Web DDoS Tsunami attacks.
- Adapt protection immediately – The solution should leverage behavioural analysis and real-time signature generation to immediately detect HTTPS floods and continuously adapt the mitigation to prevent downtime.
- Provide consistent protection – An automated, fully managed solution helps block sophisticated attacks consistently across all applications and environments.
Organisations can no longer take for granted that standard WAFs or network-based DDoS mitigation will provide adequate cyber protection. Today's Web DDoS Tsunamis are demanding a more proactive and adaptive approach to cybersecurity. Without it, organisations are simply being overwhelmed and outmanoeuvred by more emboldened threat actors with more aggressive attack plans.

