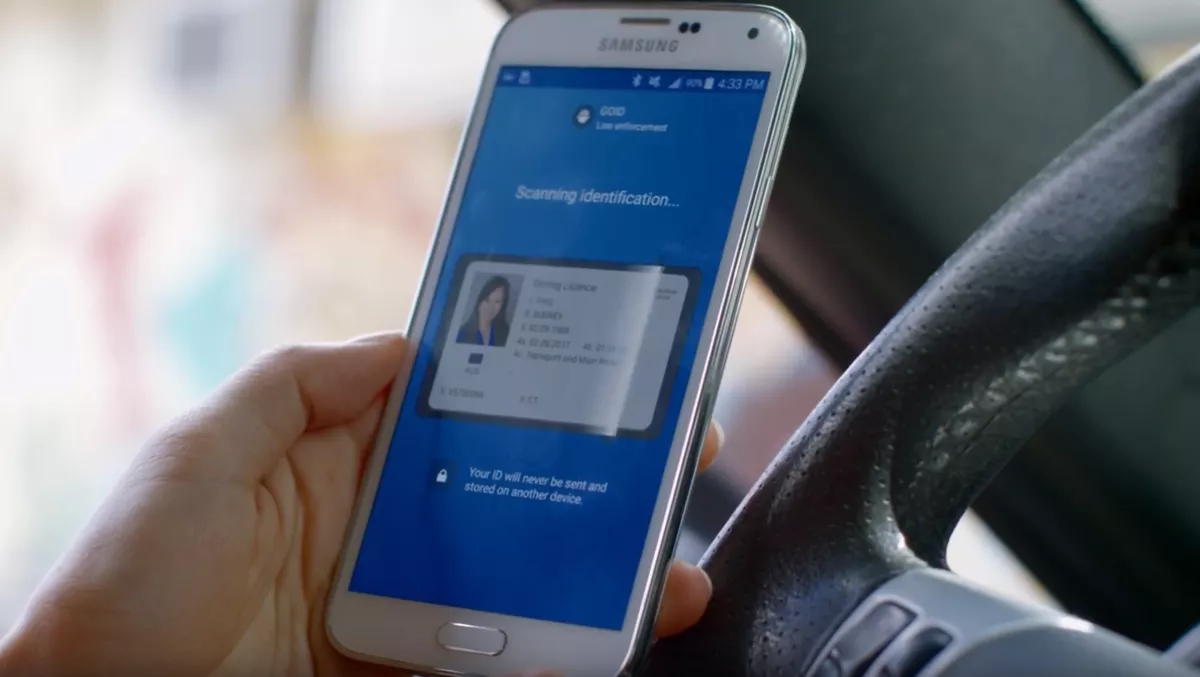
Identity solutions provider HID Global has today announced it has extended the capabilities of its HID goID mobile identity solution that enables government agencies to move from physical documents to mobile IDs on citizens' smartphones.
The latest addition to HID's mobile identity offering, the HID goID Simple Verifier, is a small device that can be used by anyone seeking to quickly verify the age of citizens carrying a HID goID mobile ID on their smartphones with one click.
“The Simple Verifier is ideal for institutions and private sector establishments such as bars, clubs and any entity that must verify customers' ages before permitting entry or the purchase and consumption of alcohol,” says HID Global citizen ID business product marketing senior director Steve Warne.
“In addition to enabling the private sector to combat fake ID attempts, the latest addition to HID goID is a powerful digital verification tool that supports governments' broader age-restricted products and services initiatives geared towards protecting the health, safety and wellbeing of minors.
After connecting via Bluetooth to the HID goID Simple Verifier, the device confirms age by securely sending a random code to the citizen's mobile ID on their smartphone.
The citizen's age is confirmed with no scanning, tapping or any other action required.
Because the solution only verifies the age of the mobile ID holder, the process is quick and efficient. It also protects citizen privacy since no additional information beyond the legal age of the citizen is shared.
Easily carried in a pocket or on a keyring, the new device joins a family of HID goID verification options that include solutions for PCs and servers, and purpose-built mobile verifiers for large-scale applications.
About HID Global
HID Global powers the trusted identities of the world's people, places and things. It aims to make it possible for people to transact safely, work productively and travel freely.
HID's identity solutions give people convenient access to physical and digital places and connect things that can be identified, verified and tracked digitally.
Millions of people around the world use HID products and services to navigate their everyday lives, and over 2 billion things are connected through HID technology.
It works with governments, educational institutions, hospitals, financial institutions, industrial businesses.
Headquartered in Austin, Texas, HID Global has over 3,000 employees worldwide and operates international offices that support more than 100 countries.