As Asia-Pacific organisations continue to migrate to the cloud and enable remote work and BYOD, the complexity of keeping sensitive data secured continues to grow.
Enterprises that fail to adapt to the modern business world when it comes to security are likely to fall prey to data breaches and experience a host of other problems.
To prevent this, organisations must have total threat protection and governance over corporate data as employees access it from remote locations and even personal devices. By leveraging a secure access service edge (SASE) offering, preferably a combination of CASB, SWG, and ZTNA, organisations can secure managed applications, web traffic and on-premises resources.
For example, let's say Karla, a marketer, attempts to use her personal computer or phone to access a sensitive file in Box that Mark, a member of HR, sent her.
If she accesses this on an unmanaged device without data loss prevention tools in place, it could lead to a security breach. This is where cloud access security broker (CASB) technology comes into play; it enables the IT team to provide secure access to cloud resources on managed and unmanaged endpoints.
Scenarios similar to that one are becoming more and more common as organisations increasingly adopt cloud, BYOD and remote work.
Below is a screenshot of security policies that can be enforced with a CASB vendor, based on variables like a user's group, access method, device type, and location, with the action column showing the kind of protection that will be enforced. In the first row beneath the header, it shows that users on managed devices will be given direct app access; the third row shows that people accessing Office 365 via ActiveSync (mobile) will undergo secure app access, with DLP measures applied at upload and download.
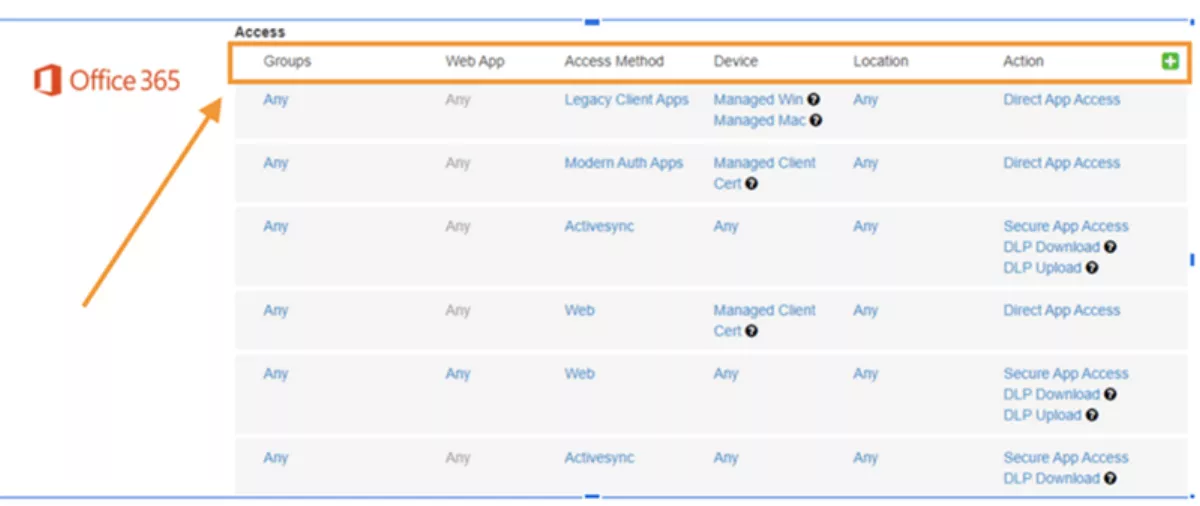
Now let's say that Mark, the HR worker, accesses Workday and attempts to upload a file that he does not know is infected with malware. Advanced threat protection (ATP) is an integral part of CASB technology and enables enterprises to identify and remediate malware in real-time.
By leveraging partnerships with leaders in the AV space, a CASB vendor can use advanced, behaviour-based detections to identify and block even zero-day malware at upload, at download and at rest. This is a unique capability that cannot be obtained with reactive, signature-based protections.
Policies that accomplish this are easily configurable within a selected vendor's dashboard. Admins choose the malware data pattern and block just like the figure below. This way, when employees fail to implement best security practices, ATP can stop malware in its tracks.
Identity management and proper authentication are the cornerstones of security and are needed for granular, contextual data protection policies.
Vendors that provides single sign-on (SSO) natively as well as integrate with other leading identity providers should be sought out. SSO serves as a single point of authentication for users accessing cloud resources.
Additionally, step-up multi-factor authentication (MFA) can be used to confirm the identity of every user exhibiting unusual behaviour or accessing sensitive corporate information in the cloud.
As a part of a SASE platform, CASB technology can provide cross-app visibility through detailed logs of all cloud transactions, including logins, uploads, and downloads.
When employees like Mark or Karla interact with applications, all file, user and app activity is logged. Detailing all interactions in the cloud enables audit, assists with demonstrating regulatory compliance, and ensures that security policies are working correctly.
Chosen vendors give administrators activity logs that display which users are accessing sensitive data when it is being accessed, which applications are being utilised, as well as what type of documents are being downloaded and when DLP policies are triggered.
With data protection, threat protection, identity management and full visibility, organisations can rest assured that they have proper security over their managed SaaS and IaaS instances.
However, CASB is only one piece of the puzzle for consistent, comprehensive protections. Secure web gateway (SWG), another essential component of enterprise security.
With a comprehensive SASE platform, organisations can keep pace with cloud adoption, remote work, BYOD, and more.


