
Security alert: More than 2 million IoT devices are now junk
More than two million security cameras, baby monitors, and smart doorbells are affected by security vulnerabilities that could allow cybercriminals to hack devices and spy on homes, according to one security researcher called Paul Marrapese.
The bad news is that there's very little anyone can do to fix the issue, besides buying new devices.
Some of the affected brands include Coolcam, Eye Sight, HiChip, HHVCAM, NEO Coolcam, Sricam, SV3C, VStarcam, and Wanscam. These devices use a component called iLinkP2P, which is also present in hundreds of other brands, so tracking down exactly what brands and devices are affected is a bit on the tricky side, says Marrapese.
"Also to note is that the number of affected devices is much higher than just two million, that is the number of devices visible outside of firewall, but this serial number brute forcing also allows to access cameras behind firewalls," adds F-Secure Labs principal researcher Jarno Nimela.
The vulnerabilities lie in the iLnkP2P, developed by a company called Shenzhen Yunni Technology Company. iLnkP2P is a way for users to connect to their devices without involving any manual configuration. iLnkP2P uses a serial number called a UID to allow users connect instantly through phone or computer.
Unfortunately, CVE-2019-11219 details a vulnerability in iLnkP2P that allows attackers to find online devices and connect to them. CVE-2019-11220 is a vulnerability that allows attackers to steal the device's password and take full control of it.
While device vendors were advised back in January it seems that they haven't done anything to acknowledge the vulnerabilities, which is why Marrapese decided to make the vulnerabilities public.
Here's how to tell if your devices are affected:
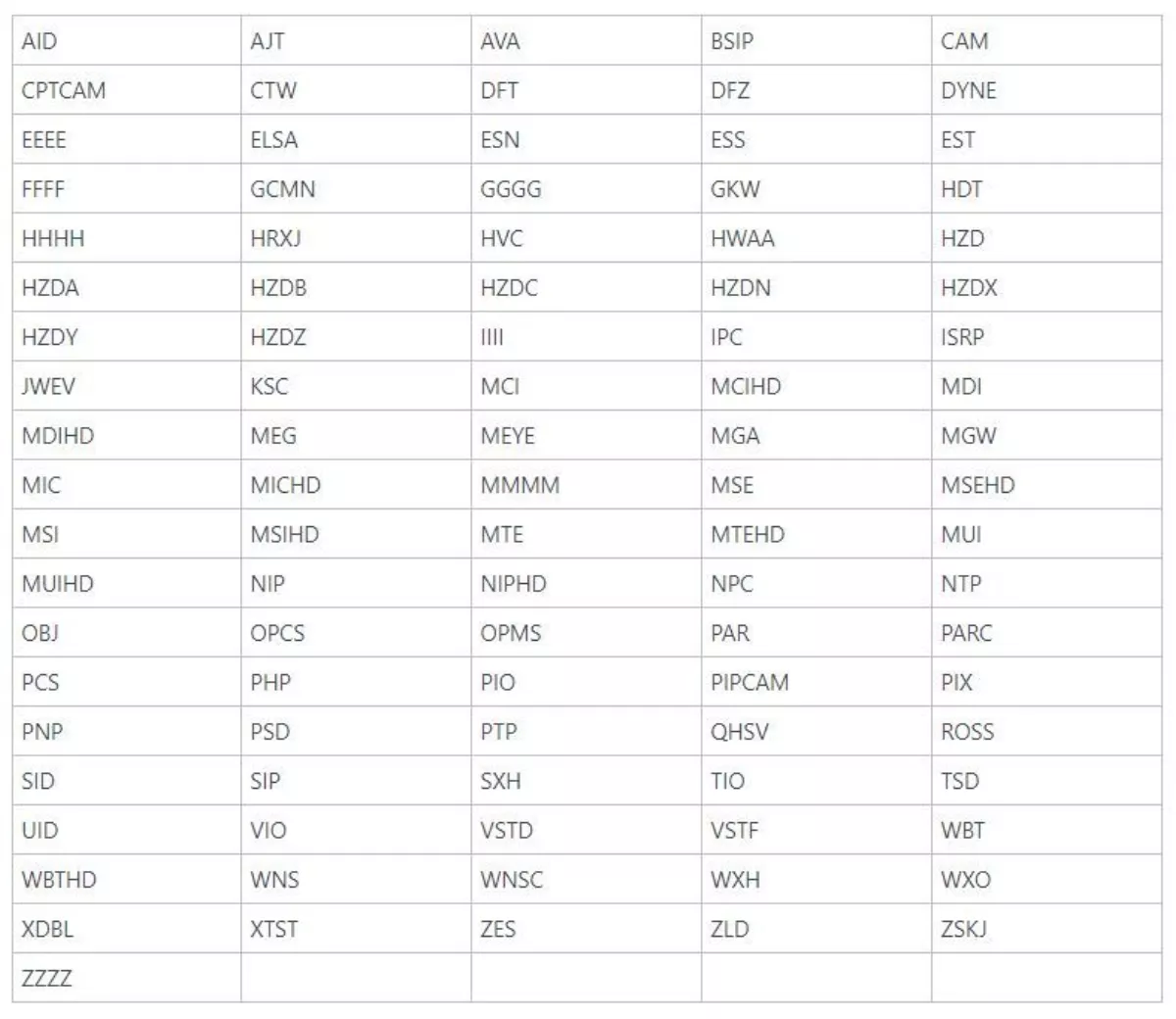
First, look for a serial number on your device called a UID. Typically, it will follow this letter-number-letter format: FFFF-123456-ABCDE
Devices with the following four letters are known to be vulnerable (keep in mind that many more vulnerable devices beyond the ones below also exist).
If your device is affected, Marrapese says outright that you should buy a new device from a vendor with a good reputation, because it's unlikely that these affected devices will be patched. The same affected devices may also be plagued with other security threats.
"If disposing of the device is not possible, the P2P functionality may be effectively neutered by blocking outbound traffic to UDP port 32100. This will prevent devices from being accessed from external networks via P2P (though local access will still work)," concludes Marrapese.


