Apple Pay “brandjacked” in new phishing attack
As cybercrime evolves and becomes more complex, cybercriminals are increasingly mimicking well-known brands and trusted companies, brandjacking them in a bid to infect computer systems and to steal sensitive data.
Apple Pay is the latest victim, with legitimate-looking receipts purporting to be from the company hitting Australian inboxes Thursday morning (AEDT).
These are actually phishing emails designed to steal confidential personal and billing credentials, like the victims' Apple ID and password, mobile phone numbers, credit card data, and similarly valuable information.
Titled 'ApplePay (Automatic Payment)', the email uses a display name of 'support@'. The body of the text appears as an official copy of an Apple Pay receipt, informing recipients of an 'integrated purchase'.
Several of the links within the email lead to a copy of the Apple login page.
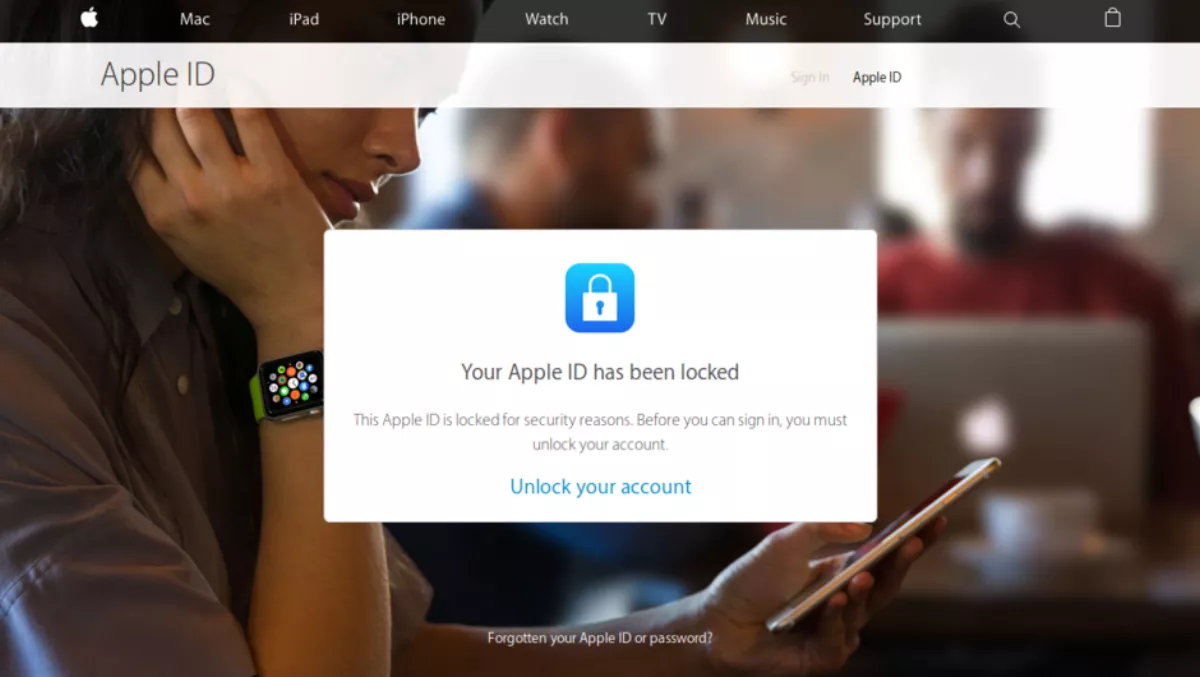
The page first asks the user to enter their Apple ID email address and password. Having given their Apple ID information, victims are led to another page informing them their account is locked.
Users who click on the 'unlock your account' link are led to another page purporting to be from Apple, requesting their billing details.
Another page then follows, requesting 'additional information' from users.
This includes their credit card information.
As the last step, unsuspecting recipients are asked to enter a one-time authorisation code sent to their mobile numbers.
Having undergone all the above steps, users are finally led to a page informing them their account is 'verified' and they are redirected to the legitimate Apple login page.
MailGuard has determined that this email actually comes from one of two compromised accounts, and understands the domain used to host the fake Apple site was registered in the past 24 hours for the purpose of this scam.
The inclusion of Apple Pay's logo and branding, along with the presence of a seemingly secure and 'official' multiple-step procedure to verify accounts, are tools adopted to boost the authenticity of the email.
Having convinced recipients that the email is actually from Apple Pay, cybercriminals exploit the trusted reputation of the brand to trick the company's immensely large customer base into divulging their confidential data.
What is "phishing?"Phishing is the practice of tricking email recipients into revealing personal information that criminals can exploit for gain.
Phishing emails go to a wide group of random people.
The attackers know that not everyone will respond, but they know that if they send enough emails out somebody will probably take the bait.
A phishing attack message will typically include a link that will send the unwary victim to a fake login website.
Once there, the user will be asked to enter username and password data which will be automatically captured by the phishing page.
Scammers use phishing pages to collect login credentials for email accounts, bank accounts, and a wide range of other online services.
Commenting on the scam, Australian cybersecurity MailGuard CEO and founder Craig McDonald says, "This is very cleverly executed scam. Not only does it mimic a major household brand like Apple, that nearly everyone online has a relationship with, but the mechanics it employs to extract sensitive data and credentials are also executed seamlessly.
"Starting with a simple email receipt, the email entices curious recipients to click through to authentic looking landing pages that trick users into handing over contact details, birth dates, mobile phone numbers and credit card info.
"All extremely useful to perpetrate identity fraud, or for re-sale on the dark web.
"Anyone that receives an Apple email should be extremely vigilant and check its authenticity before providing any confidential information online.

